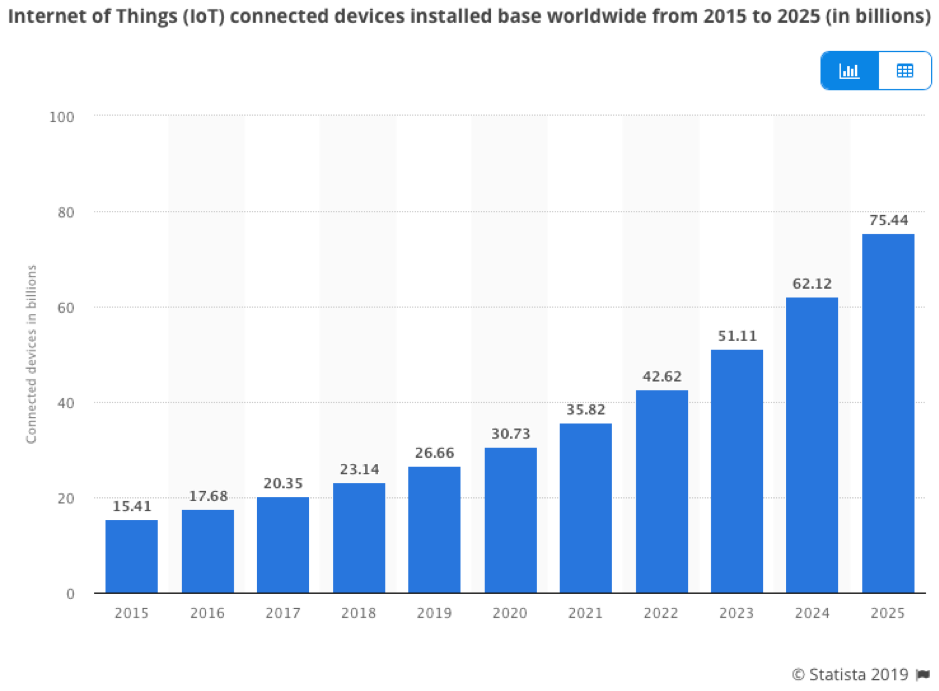
The number of IoT devices around the world keeps on growing. Globally, there are now more than 26 billion connected devices, according to research from Statista – up from 15 billion in 2015 – with the number projected to rise to over 75 billion by 2025. In 2018, the global IoT market stood at about $164 billion, and is expected to increase almost tenfold over the next six years, reaching around $1.6 trillion by 2025. The popularity of IoT technology is drastically transforming how society functions and how businesses are run. Be it manufacturing, transportation, telecoms, logistics, retail, insurance, finance or healthcare, the vast proliferation of IoT technology is on course to disrupt practically every industry on the planet. However, as more and more IoT devices are deployed across the enterprise, new challenges emerge for developers – and securing IoT systems is chief among them.
IoT in the Enterprise
Although much media attention surrounding IoT has focused on consumer products – smart speakers, thermostats, lights, door locks, fridges, etc. – some of the most exciting IoT innovations are coming from the business sector. The combination of sensor data and sophisticated analytical algorithms is allowing companies in a broad range of industries to streamline operations, increase productivity, develop leading-edge products, and solve age-old business problems. Consider the performance of all types of equipment and machinery – from jet engines to HVAC systems – being constantly monitored with sensors to predict the point of failure and avoid downtime automatically. Or how about driver speed behavior information being shared in real-time with an insurer – or geolocation beacons pushing targeted advertisements and marketing messages to customers when they are in or near a store. Usage of data from IoT sensors and controllers for better decision making – combined with automation for better efficiencies – is enormously valuable. As such, more and more businesses are getting on board with the IoT revolution.
84% of the 700+ executives from a range of sectors interviewed for a Forbes Insights survey last year said that their IoT networks had grown over the previous three years. What’s more, 60% said that their organizations were expanding or transforming with new lines of business thanks to IoT initiatives, and 36% were considering potential new business directions. 63% were already delivering new or updated services directly to customers using the Internet of Things.
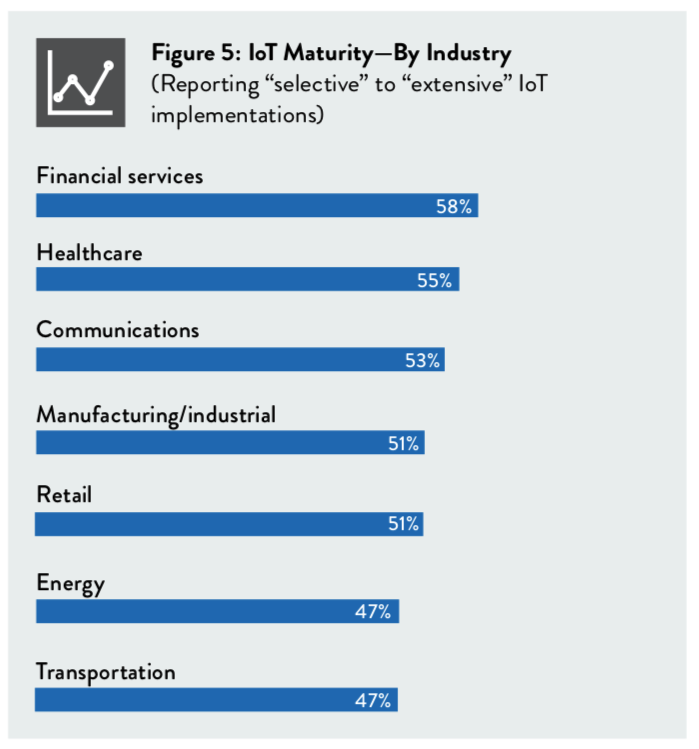
By industry, nearly six in ten (58%) executives in the financial services sector reported having well-developed IoT initiatives, as did 55% of those in healthcare, 53% in communications, 51% in manufacturing, and 51% retail.
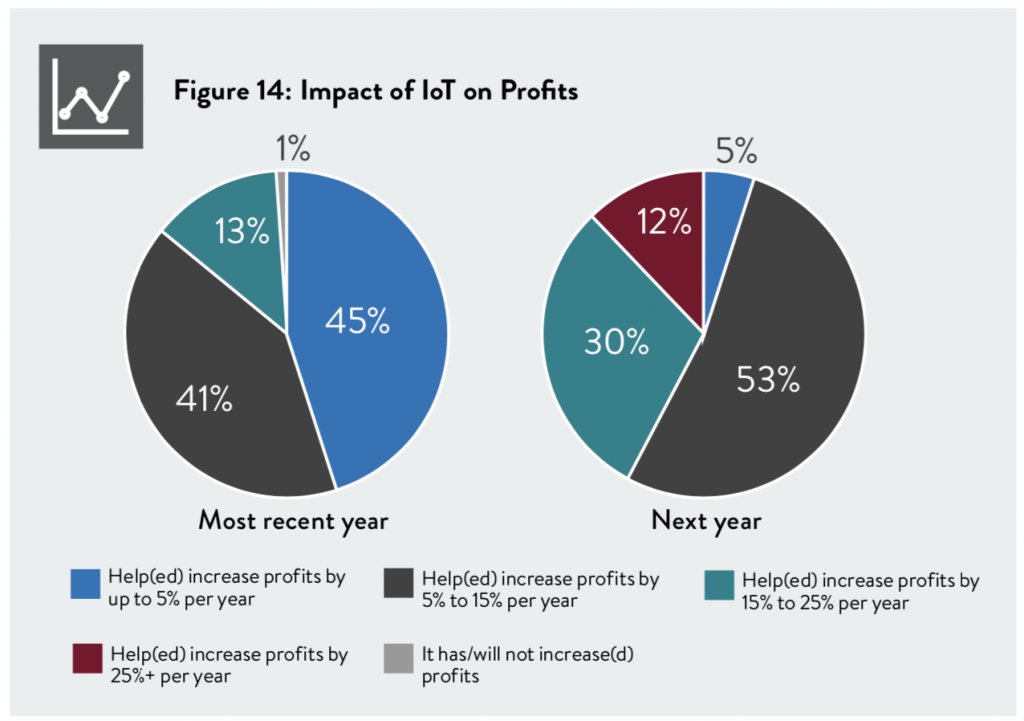
The survey also showed that leveraging IoT as part of a business transformation strategy increases profitability. 75% of leading enterprises credited IoT with delivering increased revenue. 45% reported that the Internet of Things had helped boost profits by up to 5% over the previous year, another 41% said that it had boosted profits by 5% to 15%, and 14% had experienced a profit boost of more than 15% – and all anticipated IoT to have a significant profit-boosting impact in the year ahead.
However, key to profitability and business success with IoT technology is security. Indeed, along with developing/maintaining appropriate algorithms/software and speed of rollout, securing IoT was as one of the three top IoT challenges cited by the executives. How do organizations ensure the integrity of their IoT data? How do they ensure that the various operational systems being automated with the technology are controlled as intended? These are questions that need to be answered, for a lot of hard IoT security lessons have been learned in recent years.
Securing IoT in the Enterprise – An Ongoing Challenge
As the number of connected IoT devices in the enterprise increases, new threats emerge. Distributed Denial of Service (DDoS) attacks provide a number of high-profile examples. Here, vulnerable connected devices are hijacked by hackers and used to send repeated and frequent queries that bombard the Domain Name Server (DNS), causing it to crash. For instance, the Mirai botnet in 2016 shut down major internet providers in North America and Europe by taking over hundreds of thousands of IoT devices – mainly IP security cameras, network video recorders and digital video recorders – and using them for a DDoS attack.
Mirai was able to take advantage of these insecure IoT devices in a simple but clever way – by scanning big blocks of the internet for open Telnet ports, then attempting to log in using 61 username/password combinations that are frequently used as the default for these devices and never changed. In this way, it was able to amass an army of compromised CCTV cameras and routers to launch the attack. Perhaps most concerning of all, however, is that the Mirai botnet source code still exists “in the wild”, meaning that anyone can use it to attempt to launch a DDoS attack against any business with IoT implementations – and many cybercriminals have done just that.
Another example involves a US university in 2017, which suddenly found over 5,000 on-campus IoT devices – including vending machines and light bulbs – making hundreds of DNS queries every 15 minutes to sub-domains related to seafood. The botnet spread across the network and launched a DDoS attack, resulting in slow or completely inaccessible connectivity across the campus. Again, it was weak default passwords that left these devices vulnerable.
One of the main problems with IoT devices being used in workplace environments is that many are not inherently secure. Part of the issue is that there are literally thousands of individual IoT manufacturing companies – many of which started life in the consumer market – with very little consistency between them. What this means is that each IoT device that ends up in the workplace – be it a lightbulb, vending machine, or CCTV camera – will likely have its own operating system. Each will likely have its own security setup as well – which will be different from every other connected thing in the office – and a different online dashboard from which it is operated. Many of these devices are also shipped with default usernames and passwords, making them inherently hackable. The manufacturers, meanwhile, take little or no responsibility if any of these devices are hacked, meaning the onus for securing IoT in all its forms falls entirely upon an organization’s IT department – and too often no one is assigned to this critical task.
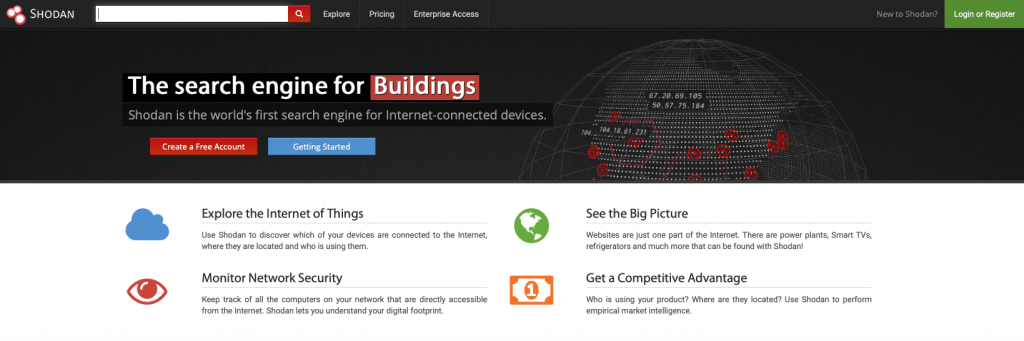
What makes it so critical? Well, thanks to Shodan – a specialized search engine that lets users find information about IoT devices (including computers, cameras, printers, routers and servers) – anyone, including hackers, can locate devices that use default logins with a simple web search. However, what’s good for hackers can be seen as being good for enterprises, too. Though the very existence of Shodan is perhaps scary, IT professionals should be using the search engine proactively as a security tool to find out if any information about devices on the company’s network is publicly accessible. After that, securing IoT is down to them.
Another issue that renders securing IoT devices absolutely essential is the threat of spy tech and ransomware. Many IoT devices incorporate microphones, cameras, and the means to record their location, leaving organizations vulnerable to sensitive data being stolen or company secrets being exposed and held to ransom. Things like IoT-enabled building management systems can also be left open to surveillance or meddling from malicious third parties. A hacker could, for instance, lock all the doors in an office building or cut all the power. As an example, researchers at Def Con demonstrated how such a system can be targeted with ransomware by gaining full remote control of a connected thermostat. In a real-life scenario, such an attack could result in an office becoming uninhabitable, opening an organization up to ransom demands to regain control.
In short, with the ever-increasing number of IoT devices an organization relies upon, the attack surface grows in kind – as does the unpredictability with regards to how hackers may seek to exploit them.
The Huge Costs of Not Securing IoT
Securing IoT should be a top priority for practically all businesses for the simple reason that practically all businesses are invested in IoT. In fact, according to recent research from DigiCert – State of IoT Security Survey 2018 – 92% of organizations report that IoT will be important to their business by 2020. The executives interviewed cited increased operational efficiency, improving the customer experience, growing revenue, and achieving business agility as the top four goals of their IoT investments.
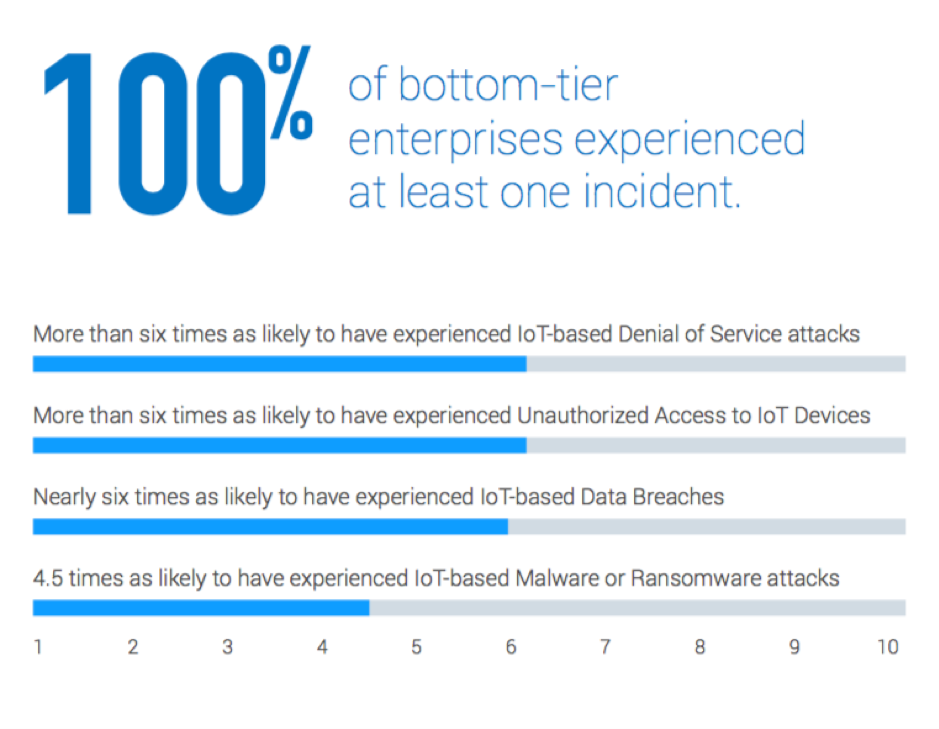
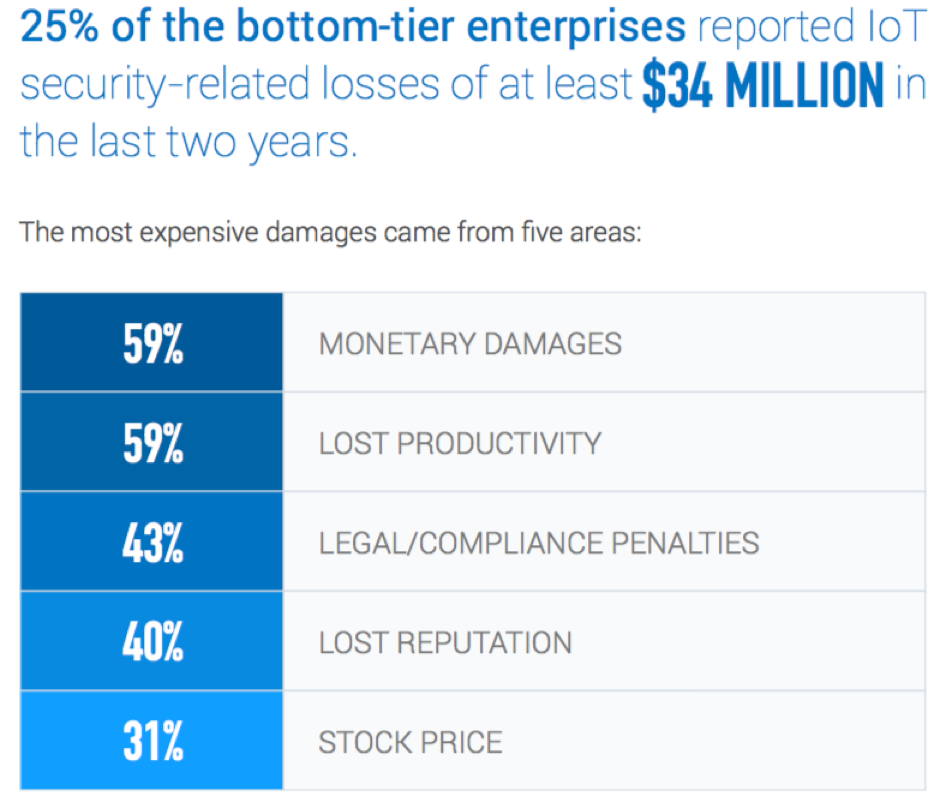
However, securing IoT remains the biggest concern for 82% of these organizations. And it’s no wonder – a full 100% of bottom-tier enterprises (i.e. enterprises that are having the most problems with IoT security issues) had experienced at least one IoT security incident in 2018. Of these, 25% reported related losses of at least $34 million over the previous two years.
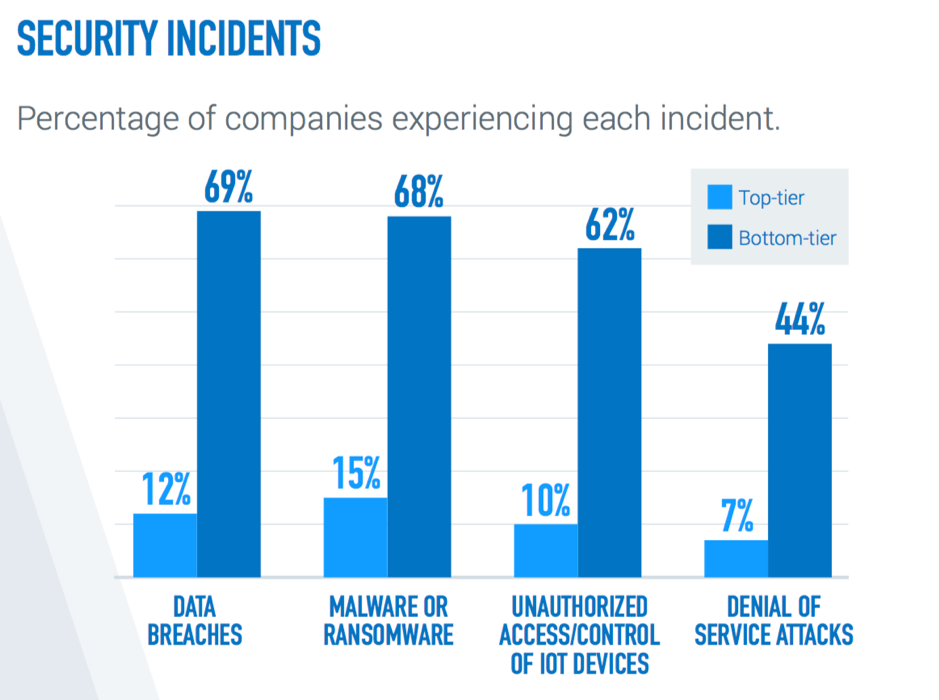
These bottom-tier companies are much more likely to experience data breaches, malware/ransomware attacks, unauthorized access/control of IoT devices, and IoT-based DDoS attacks than top-tier companies (i.e. companies that are best prepared in terms of IoT security). So – what are top-tier companies doing differently? Well, DigiCert found that they all had five key behaviors in common – they were all ensuring device data integrity (authentication), implementing scalable security, securing over-the-air updates, utilizing software-based key storage, and encrypting all sensitive data.
Speaking to Security Now, Mike Nelson, Vice President of IoT Security at DigiCert, comments on the findings: “The security challenges presented by IoT are similar to the many IT and internet security challenges industries have faced for years. Encryption of data in transit, authentication of connections, ensuring the integrity of data – these challenges are not new. However, in the IoT ecosystem these challenges require new and unique ways of thinking to make sure the way you’re solving those challenges works. Regarding evolution of security challenges, the biggest challenge is simply the scale and the magnitude of growth. Having scalable solutions is going to be critical.”
Final Thoughts
IoT has the potential to open up many new opportunities for growth and agility within the enterprise. However, securing IoT devices remains absolutely crucial. Organizations need to take the necessary steps to ensure that their devices and data are adequately protected from end to end. This will involve conducting a thorough review of the current IoT environment, evaluating the risks, and prioritizing primary security concerns that need to be addressed. Strong and unique passwords must also be mandatory for every device. Firmware must be constantly updated, and only secure web, mobile and cloud applications with strong encryption and data protection features must be used. All data must be encrypted – both at rest and in transit – with end-to-end encryption made a product requirement for all devices that connect. It’s also important that this data is secured and processed securely after it has been transmitted across the network. Device updates must be monitored and managed around the clock and around the calendar. Finally, the security framework and architecture must be scalable to support IoT deployments both now and in the future. As such, working with third parties that have the resources and expertise to manage scaling IoT security programs will be invaluable.
Vinnter serves as an enabler for developing new business and service strategies for traditional industries, as well as fresh start-ups. We help companies stay competitive through embedded software development, communications and connectivity, hardware design, cloud services and secure IoT platforms. Our skilled and experienced teams of developers, engineers and business consultants will help you redefine your organization for the digital age, creating new, highly-secure connected products and digital services that meet the evolving demands of your customers. Get in touch to find out more.





